- 08 Nov 2023
- 5 Minutes to read
- Print
- DarkLight
- PDF
Ransomware-Proof Data Recovery for Cyber Resilience
- Updated on 08 Nov 2023
- 5 Minutes to read
- Print
- DarkLight
- PDF
Ransomware

Businesses are increasingly under attack from cyber threats in the form of ransomware, spear phishing, and malware. Ransomware is a huge global threat to businesses around the world. Businesses are projected to have paid out $20B in 2021, a 100% Y-o-Y increase for the last four years, and it’s only going to get worse with new business models like RaaS: ransomware-as-a-service. When an attack starts, organizations need to detect ransomware as early as possible to stop the threat and remediate those resources.
SMBs and large businesses need three layers of defense:
- Protection: A backup target that allows them to lock backups for a designated time period for immutable backups.
- Detection: An algorithm for detecting changes in the source volumes that is outside of expected variance for behavior-based monitoring.
- Recovery: A recovery path that can restore entire systems but exclude affected files.
Retrospect Backup provides ransomware protection and detection capabilities with Immutable Backups and Anomaly Detection combined with ransomware-proof recovery to restore systems without affected files for cyber resilience.
Protection: Immutable Backups
Cloud Object Lock locks files for a period of time. Because cloud storage providers like Amazon S3 control the API, they can add features like Object Lock, also referred to as Write-Once-Read-Many (WORM) storage or immutable storage. This lock is a retention policy for a specific version of a file that is locked from changes from every user, including the administrator. You can think of this as a virtual air-gap in the cloud because there is no way, barring to close the account, to delete that file before the retention date is passed.
Retrospect Backup uses Object Lock to create Immutable Backups. These backups are locked for a specific amount of time. Users can set a retention period for backups stored on supporting cloud platforms. Within this immutable retention period, backups cannot be deleted by any user, even if ransomware or a malicious actor acquires the root credentials.
Using ProactiveAI for advanced scheduling logic, Retrospect provides a rolling window of immutable backups, combining forever-incremental backups with point-in-time restores even after the initial backup passes out of the immutable retention policy.
Retrospect Backup’s ransomware protection is certified with Amazon S3, Microsoft Azure Blob Storage, Google Cloud Storage, Wasabi, Backblaze B2, and MinIO.
For more information about ransomware protection with Retrospect Backup, see
Detection: Anomaly Detection
Organizations need to detect ransomware as early as possible to stop the threat and remediate those resources. Anomaly Detection in Retrospect Backup identifies changes in an environment that warrants the attention of IT.
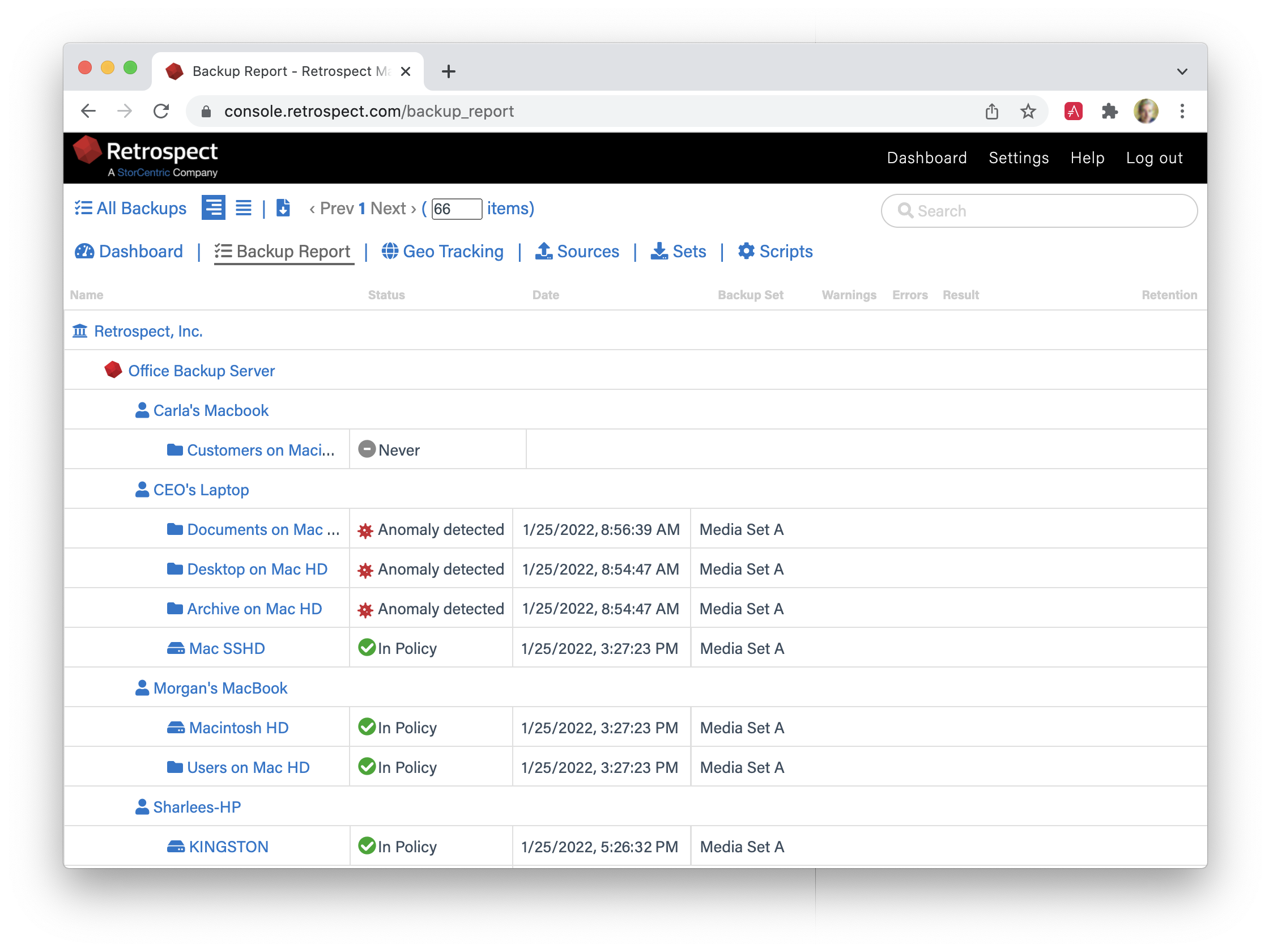
Administrators can tailor anomaly detection to their business’s specific systems using customizable filtering and thresholds for each of their backup policies, and those anomalies are aggregated on Retrospect Management Console across the entire business’s Retrospect Backup instances or a partner’s client base with a notification area for responding to those anomalies.
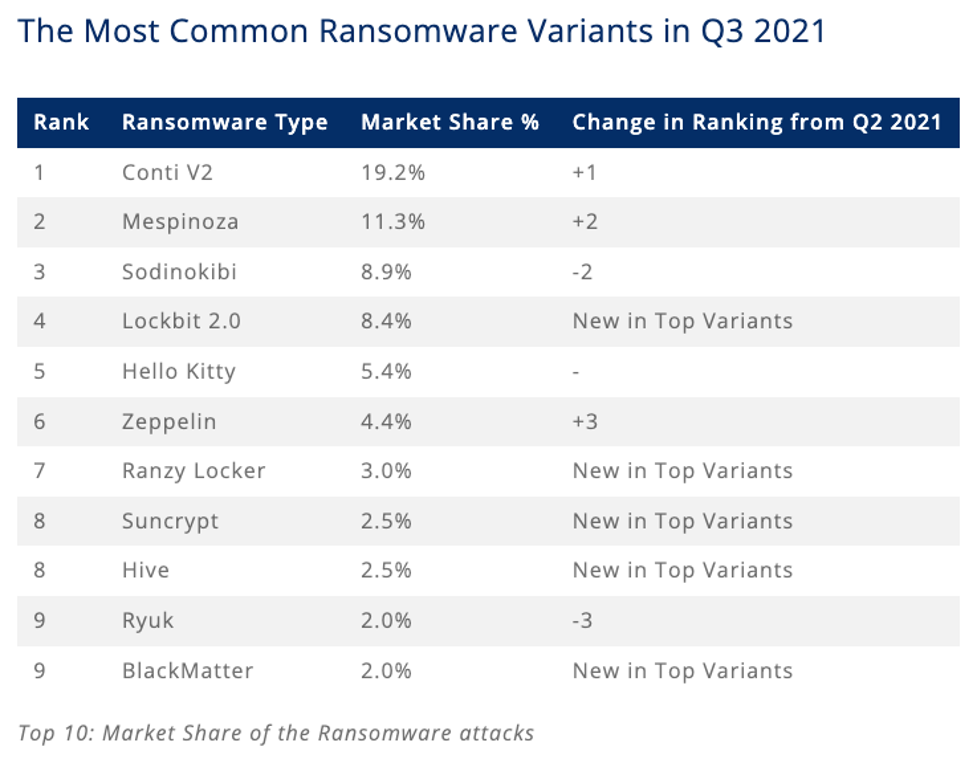
Retrospect Backup detects all of the major ransomware variants using an algorithm that focuses on file metadata anomalies. According to Coveware, the top variants are always changing, with over 50% changing every quarter. The key to detection is combining technologies such as signature detection in processes with file-based irregularities. Using a multi-pronged defense, with immutable backups, anomaly detection, and other security layers, businesses will know when they’re being attacked and will have the tools to remediate it and move on.
- Filtering: Configure a filter to identify the files to observe. Retrospect lets administrators tailor this to file types, paths, dates, or specific attributes, and the built-in filter focuses on office documents, photos, and movies.
- Threshold: Set the threshold for the alert. If the percentage of files new or changed out of the total number of files matched by the filter is greater or equal to the threshold, Retrospect will create an anomaly event.
- Notification: Access notifications on Retrospect Management Console, receive them immediately in an email, and find them in the Execution History and Backup Report. Retrospect surfaces the notification for anomaly detection in the best place for an organization.
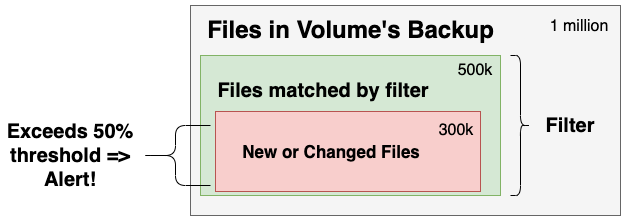
The diagram shows the volume being monitored as a whole, the subset of files that match the "Anomaly Detection" filter, and the files that are new or changed within that subset. Retrospect generates an alert if the percentage exceeds the threshold.
For more information about anomaly detection with Retrospect Backup, see Anomaly Detection.
Recovery: Ransomware-Proof Restore
Immutable Backups and Anomaly Detection provide the tools to protect your backups and monitor your infrastructure, so that you can identify an attack and remediate the affected devices.
The best case scenario is that you can perform a point-in-time restore from an immutable backup from a time before that ransomware started. You can do this in Retrospect for a set of files and folders or as a disaster recovery (DR) scenario for an entire system, also known as bare-metal recovery (BMR). For DR, Retrospect enables you to restore the backup to the original machine or to a new system with dissimilar hardware restore.
For a file-level recovery, Retrospect allows you to restore the set of files and folder to the original location or to a new one and supports fine-grained options. For instance, you can restore the set of files to a location that already contains a subset of those files, and you can choose whether to overwrite the existing files or only copy missing or newer versions of the file. With Retrospect, you have powerful capabilities to tailor your recovery to your environment.
However, let’s say the worst happens. You identify ransomware that has slowly encrypted a system, and you have no unaffected backups. With Retrospect, you can still recover that full system for a ransomware-proof restore. While the backups contain ransomware and files encrypted by ransomware, with Retrospect, you can use file-based data filtering during the restore process to exclude those bad files from the restore.
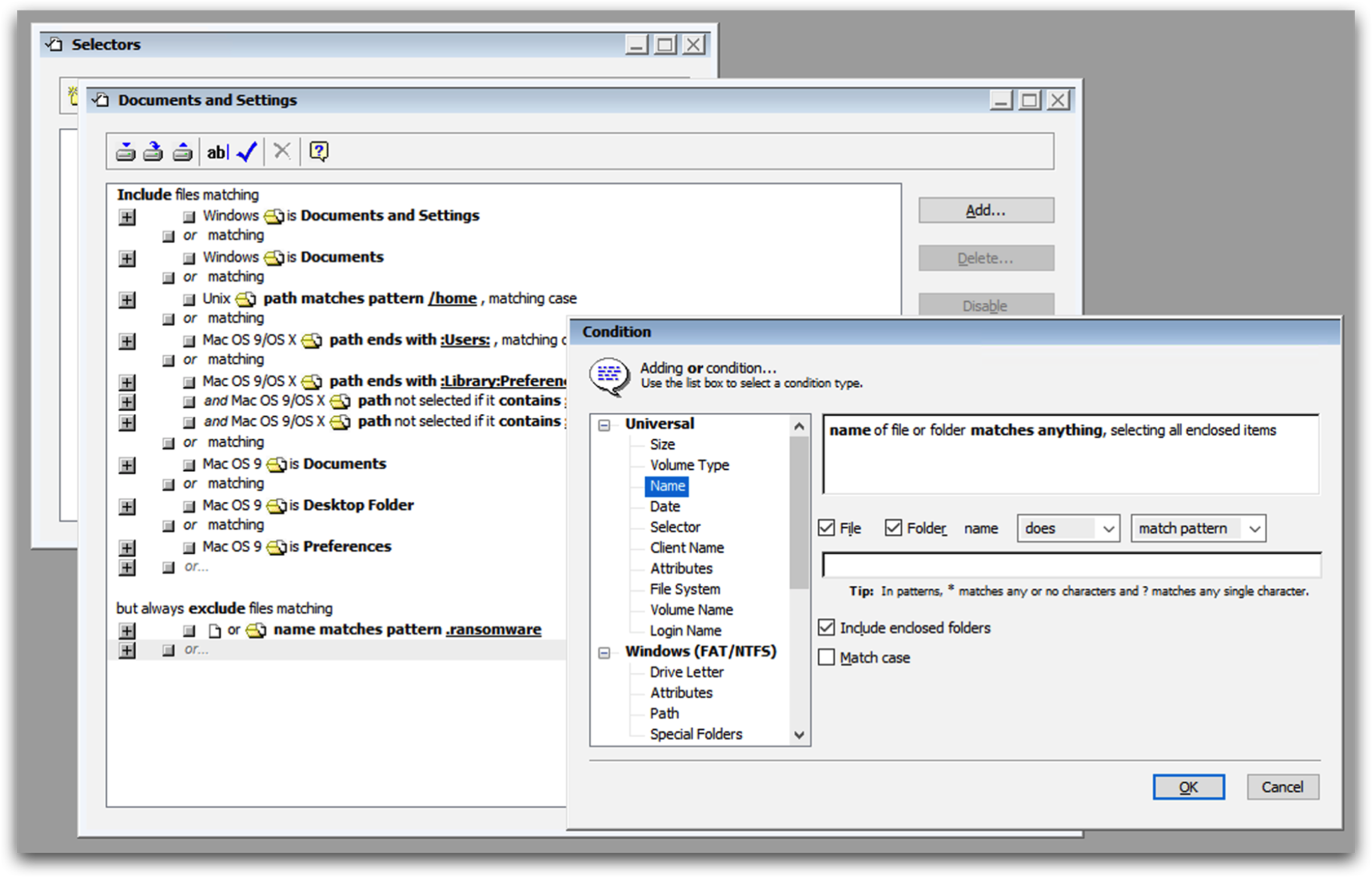
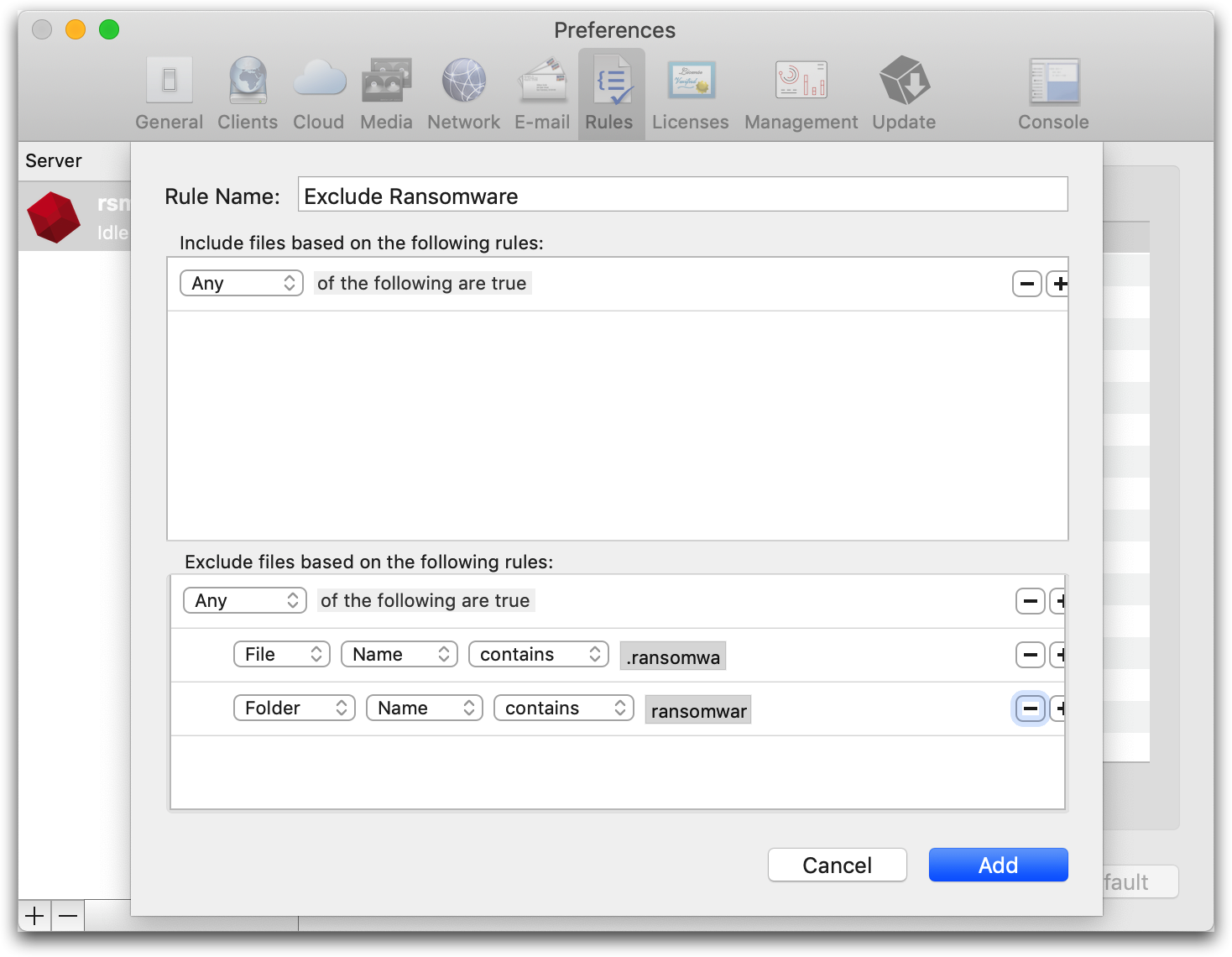
You can construct a data filter, called a "Selector", that is customized to your restore. These filters are supported for both full DR system recoveries and for small file-and-folder restores. In the filter, add exclusion clauses for all the files that have the ransomware’s extension and for the root ransomware executable. When you run the restore with this filter, Retrospect will exclude the ransomware executable and affected files for a ransomware-free restore.
You can also run a “Find Files Restore” to search for any executables installed in the last month to pinpoint when the malicious ransomware was installed.
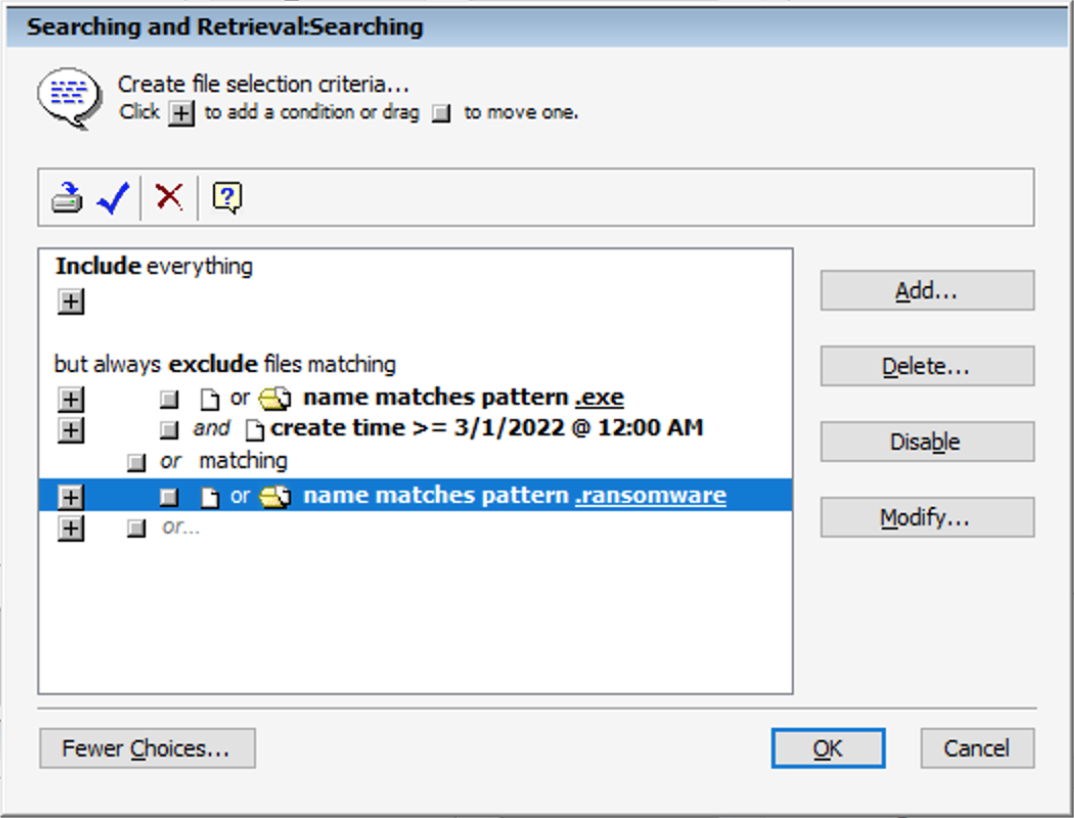
Unlike many other data protection solutions that rely on image-based backup technology, Retrospect can perform this fine-grained data filtering at a file level to enable ransomware-proof recovery. For more information, see
Last Update: February 15, 2022

